
[UPDATE] added instruction for latest firmware ver. 1.8.7.0C_201705091058
Recently I bought a Xiaomi Xiao Yi (IP) camera (also known as Yi Home), Chinese version. The camera looks nice, the picture quality is ok, and worked fine on my local Wifi.

However, I was unfortunate enough to receive and test the camera when Xiaomi decided to deny access from the iOS app to the camera outside of China (error 5400). I was hoping a firmware upgrade would solve this issue so I have upgraded from 1.8.5.1L to 1.8.6.1B. Now my camera was useless. The camera would say “This camera can only be used in China” and would shut down.
This was the tipping point when I have decided I will investigate what’s happening with this camera and what can be done to make it functional again. At the time of writing the remote access (error 5400) has been solved by the provider so no additional action is required. (I tried to convert a CN camera to international one by changing the serial of the device, but couldn’t test from a European or US IP and probably I would have needed access to the system files of a functional international camera to compare)
So the remaining issue was the camera shut down with the latest firmware (tested with 1.8.6.1A and 1.8.6.1B).
If you do a search there are heaps of websites describing how you can gain access to the camera and ultimately enable remote access via telnet. I won’t get into those details, you can check some of the websites I listed below.
Once you logged into the camera via telnet the fun part begins. The camera is running a Linux version.
# uname -a Linux (none) 3.0.8 #1 Wed Apr 30 16:56:49 CST 2014 armv5tejl GNU/Linux
This is familiar territory, we can check what processes are running, log files, the /home directory and we can mess around with the system. I have to mention this is for educational purposes only and you can easily brick your camera.
Back to the “This camera can only be used in China” message. So if you look carefully in the log file “/tmp/log.txt” at some point you will see the forbidden.g726 sound being played and not long before that there is an API call to the mothership to check if your device is allowed to run on not. With this call, the camera sends your IP automatically so there is not much to be done about that.
[/home/cloud][4/29/22:51:48:52]: req_info=https://api.xiaoyi.com/v4/ipc/check_did?hmac= danger danger danger danger danger%3D&seq=9
&uid= danger danger danger dangerXX×tamp=4294938554
{"allow":false,"code":"20000"}
Now the nice thing about this is that we can fake the response from the server in many different ways.
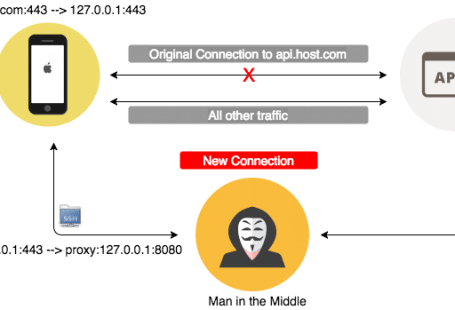
1. You set up a proxy to be used and the proxy will change the reply from “allow”: false to true. The certificate on the camera can be changed so you can set up a valid proxy for https request for a man in the middle attack. (/home/ca.crt). Possible but too complicated and you need a proxy running.
2. You can set up a fake response on the camera via the local HTTP server and redirect (see point 3 😉 ) the check_did call to this file. (/home/web/response.json -> {“allow”:true,”code”:”20000″}). Again possible but not really needed.
3. And finally, we got to the solution. In the log files, we saw that /home/cloud is responsible for checking the permission for our device. This is a binary file and we can check what calls are made from this file:
# strings /home/cloud | grep http http://log.xiaoyi.com/info.gif?p=home_v1&sysVersion=%s&mac=(lots' of other details) %s -c 311 -url https://api.xiaoyi.cox/v4/ipc/check_did -uid %s -keySec %s %s -c 139 -keySec %s -url https://api.xiaoyi.com/v4/ipc/reset -uid %s -version %s -mac %s ...... %s -c 138 -key %s -keySec %s -url https://api.xiaoyi.com/v4/ipc/on_line -uid %s -version %s -mac %s -packetloss %d -p2pconnect %d -p2pconnect_success %d -tfstat %d %s -c 136 -url http://api.xiaoyi.com/v2/ipc/sync_time (yes, the camera logs and sends everything back to xiaomi)
Now if we change the call check_did to our local file mentioned above that would make /home/cloud happy and the camera will run. Luckily /home/cloud will lock your device just if the remote server replied with “allow”: false. Now, all we need to do is to block that call or break/invalidate that URL (ie. DNS error).
THE SOLUTION:
# ps | grep /home/watch_process | grep -v "grep" | awk '{print $1}' | xargs kill -9
# ps | grep /home/cloud | grep -v "grep" | awk '{print $1}' | xargs kill -9
# sed -i 's|api.xiaoyi.com/v4/ipc/check_did|api.xiaoyi.cox/v4/ipc/check_did|g' /home/cloud
# reboot
First commands will kill watch_process so it doesn’t restart other processes.
The second command will stop the cloud service, so we can change the file.
The third one will change the text in the binary file. It will change com to cox which will invalidate the URL and will not return the allow: false message anymore.
Once the camera reboots it will be functional just as before you upgraded to the latest firmware. In case anything goes wrong just install a fresh, unmodified firmware.
Drop me a line if this worked for you!
Update: Read the comments for CNxx160622 hardware with FW 1.8.6.1C or 1.8.6.1Q.
Serial port connection to the camera explained in this video (credit to fedeant):
1.8.6.1C and 1.8.6.1Q problem solved by JonesChi:
I wrote a scrip to make the camera work again outside China. Download the file, and decompress it to root of SD card. http://diy.2pmc.net/wp-content/uploads/2016/10/hack_yi.tar.gz
If your device’s FW is 1.8.6.1C, you just need to insert the SD card into your camera, and it will hack your device automatically, when it finished, the camera will reboot automatically, then your camera is free.
If your device’s FW is 1.8.6.1Q, you need to connect your camera via serial port to get console, then insert the SD card into your camera, when you see the command prompt, just type “/tmp/sd/hack_yi.sh”, then your camera is free.
If you are using the latest firmware 1.8.7.0C_201705091058, controsensi updated the script above to support this. The file name that needs to be uploaded to the SD card has changed to equip_test.sh and the location of the home directory in the script has changed as well. The rest seems to be functioning the same way.
Create this file on the SD card and reboot your camera. It should work without the annoying restriction message. controsensi’s full solution is described here.
[sd_card]/test/equip_test.sh
#!/bin/sh
# JonesChi's script.
# Modified by halnovemila (HalEx) to work on CN12 model
timestamp=`date`
sdcarddir=`dirname $0 | sed -n 's/\/test//p'`
testdir="${sdcarddir}/test"
logfile="${testdir}/hacklog"
echo "Current dir= ${testdir}" >> $logfile
echo "SDcard dir= ${sdcarddir}" >> $logfile
cat /home/version >> $logfile
echo "========== LIST OF /home ============" >> $logfile
ls -l /home >> $logfile
if [ -f /home/cloudAPI_real ]
then
echo "Already hacked ${timestamp}" >> $logfile
sync
else
echo "Start hacking ${timestamp}" >> $logfile
cp /home/cloudAPI $sdcarddir/cloudAPI.bak
mv /home/cloudAPI /home/cloudAPI_real
cp $sdcarddir/cloudAPI /home/cloudAPI
echo "Done hacking ${timestamp}" >> $logfile
# fix bootcycle
mv $testdir/equip_test.sh $testdir/equip_test.sh.moved
sync
reboot
fi
# ATTENTION!
# Once the script is executed the boot process is halted,
# nothing else will be executed.
# Therefore if the hack has been already applied
# and this script executed,
# the camera will not complete the boot process
# and will seem like if it's not working.
Some websites to check to see how you can enable the remote access (telnet/nc):
http://xiaoyi.querex.be/
https://yadi.sk/d/MpaQaTC1mU2kQ
http://en.miui.com/thread-224653-1-1.html
– Peter



565 comments: On [SOLVED] Xiaomi Xiao Yi Ant HOME CN12 – This camera can only be used in China (1.8.6.1 – 1.8.7.0)
i bought the camera on 10 august , i says same.
unable to flash to any version
All the Xiaoyi camera 720 with CN 20160622 and above already set hardware lock by Xiaoyi. No more upgrade/ downgrade firmware available from SD card. Any other solution push the new firmware into a camera?
any solution?
Dear erick
How to know the version like CN2016622?
Where to find it?
I have checked the 1.8.3.4J_201412291009.zip firmware with the latest CN *160622 720p camera version and I can agree with Samson Law this version has some hardware lock – or better they changed way the firmware gets updated.
Wrapup: no firmware available will fix your CN *160622 camera atm. We can pray someone at xiaomi will get concious and release all the restrictions.
If you want to check all the firmwares yourself (including the oldest 1.8.3.4J), you can download them here:
http://chomikuj.pl/cdcover/xiaomi_ant_home_camera_yi_720p_firmwares_2015,5530344856.zip
Best
cdcover
cdcover,
Download a file size greater than 1 MB ( 44.51 MB ) requires the payment of the costs of the transfer of the servers Chomikuj.pl.
Is this possible to provide download from other site?
You have 50Mb free credit Larry just reg an acc in few seconds…
Here is the Dropbox link to this file, But none of those FW works.https://www.dropbox.com/s/iay1sy0y29hrjhs/xiaomi_ant_home_camera_yi_720p_firmwares_2015.zip?dl=0
Waiting for solution 🙁
anyone have a solution for xiaoyi batch august ,it even no allow us flash the camera….
in my hand have 20pcs ….just put there ..sad.
I am sure there would be a solution to this. Unfortunately I do not own any of the new batch. I anyone is willing to borrow me one (in Sydney) I can have a look.
If anyone wants to try one idea would be to trick the mobile app to download a modified firmware and upload that to the camera.
I have some new batchdney too of this cameras, you can borrow it ti test. I am in sy
There is some 4pin serial port just between the microusb port and sdcard slot, hidden under the cover. Maybe we can direct access the cam thru this! Anyone has intel how to use it? http://www.image-share.com/ijpg-3313-83.html
Hope someone can write the hack from this port!
http://felipe.astroza.cl/hacking-hi3518-based-ip-camera/
Yi Smart Camera is based on Hi3518. You can use this to access the console.
I tried to connect the console port (which is 3 pins instead of 4 pins as the above image). Tried several settings from 115200 to 9600 8N1 as well as reverse the TX and RX. All received blank screen. Anyone can successfull login the U-Boot?
I have succeed to connect the cam via serial port with the three contact points after the connector. (Yes, not connect via the 4pin connector)
The pins are TX, RX, GND from left to right on the image.
TTL voltage level is 3.3v and baud rate is 115200.
After you get the console, you can then hack the check_did API.
Please share if anyone have solution
I have 1 connected camera that is bought last year and running firmware 1.8.5…
Plus 4 cameras bought about 2 months ago.
The new cameras didn’t work from the beginning of the installation, with the English message “can only be used within China”. So I upgraded the firmware of these 4 with the Russian patched 1.8.6. They started to work after that and I never upgraded again.
My problem is that I get the activity alerts notifications on internet, and the old camera is connected very fast with internet from the outside of the LAN, but new cameras can not be connected most of the times.
All the cameras can be connected very easy and fast when the phone is connected to my home’s LAN.
I just found that I can get fast connection to new cameras and download the motion detected videos by using China VPN.
Any ideas?
Can anyone check to what servers are the new CN17*160622 cameras connecting? I tried to block these DNS with no success:
ot.io.mi.com
api.xiaoyi.com
The yi cam sends its SN to some servers – if we only can block that!
update new last mi home app, and it work
Hi hilang,
So with the newest version u successfully use it with updated new mi home?
From a video review on youtube, I notice there’s a feature to select specific region for motion detection with the international version of yi home camera 720p.
Is this not available with the china version?
Or is it a new feature that’s added later in the latest firmware (1.8.6q)? I still haven’t updated mine yet
only inter vesion have this function cn version no have
In Q version there isn’t 🙁
I am having the international version of the camera and using it with the Yi Home app.
So far, I have not modified the firmware or done anything trickery with it whatsoever.
The setup worked fine for me using the Yi home app too.
However, I want to use the cam in the Mi Home app, together with all my other smart home stuff.
Now here is the catch, I cannot get the camera working under the Mi Home app, after the QR code has been scanned and the camera replied successfully that the code scan has been successful, the blue LED turns from the blinking state to the solid state.
This tells me, that the WiFi is working and connection was successful.
I can ping the camera’s IP and also get a response.
However, for some reason it wont get added to the Mi Home app and the camera keeps saying:
“QR code invalid please reset camera”
I have done this like a million times with the Mi Home app, but I cant get it working.
Does anyone have a idea what this could be, as it works perfectly with the Yi Home app.
Thanks in advance for any hint!
Do you use “Mi Account” in Yi Home App or you are using “Yi Account”?
I am having a Yi account for the Yi app and a Mi account for the Mi Home app. It wont let me log in trying to use the Mi account with the Yi app and vice versa.
The international Ed. of Yi Cam can not be used with Mi Home, you can use only Chinesse version.
You cannot combine the non international version with the international version because it use different apps. (Yi home). Dont know in mi home…
I need help !
Bought two Yi 720 INTERNATIONAL VERSION and only found out now it only works in Taiwan Korea and US…..
I need to use in UK. Anyone know which firmware I can download ? tried many here but none worked for mine.
Manufacturing date is 160718.
Please help !
I have the INTERNATIONAL version too and I am happily using it within New Zealand. I am using Firmware version 1.8.6.1B_201604071154_INT
Hi everyone,
I just got the CNxx160622 model and the same thing happens.
It can not be used outside of China. I tried to change firmware, telnet and nothing has worked. In one of the answers, I read something to block DNS and I said, I’ll play with the router remove Internet connection and keep my network .. to try.
Looking for the ip of my camera, with YI on, from the console windows and saying every bit “can only be used in Chinese” I look and I see the led blue stays set.
The camera is connected to the mobile application YIHOME, and I see mi hand in mobile. Just give me time has to do a screen capture mobile and stopped working. I do not know what happened, but I run a minute …. I have screenshots of what gave me time.
It has not returned to work.
YI Home 2.10.2.8_20160907
Camera: CNxx160622 with factory firmware: 1.8.6.1C_201605191103
Mobile: S6 with 6.0.1
For CNxx160622
Looks like you need to use a TTL cable to enable firmware upgrade/downgrade
anyone tried?
My first was 17CN danger danger16062 which was bricked after trying the different firmware. I returned it and received older version with 12CN danger danger160512. This is working properly with this patched firmware 1.8.6.1B.
http://www27.zippyshare.com/v/nXZP3NJY/file.html
[sys]
version=1.8.6.1B_201603181307
[kernel]
version=3-0.8
provider=18e
devtype=18e
-Able to connect wifi
-Mi Home ok
-Record and playback is ok.
I will further test it and see if there is any issue.
Sorry for typo, the first version is: 17CN danger danger160622
Here is the grep of http from the /home/cloud bin file.
# strings cloud |grep http
http://log.xiaoyi.com/info.gif?p=home_v1&sysVersion=%s&mac=%s&key=%d&didm=%d&sn=%d&tfstat=%d&hdSize=%d&hdLeftSize=%d&silentmode=%d&lightmode=%d&isdaymode=%d&packetloss=%d&out_packetloss=%d&is_video_viewing=%d&p2pconnect=%d&p2pconnect_success=%d&ssid=%s&bssid=%s&ptz_horizontal_flip=%d&workmod=%d&doreset=%d&xiaomirouter=%d&bind_success=%d&start_with_reset=%d&miio_send=%d&miio_recv=%d&motion=%d&p2ptype=%d&alarm_enable=%d&record_num=%d&systick=%u&video=%d&pic=%d&gen_url_fail=%d&gen_url=%d&error_time=%d&sync_packet_len=%d&sync_packet=%s&ban_dev=%d&cgi_check_mirouter_ok_cnt=%u&nslookup_check_mirouter_ok_cnt=%u&tnp_init_status=%d&tnp_p2p_mode_cnt=%u&tnp_relay_mode_cnt=%u&tnp_check_login_success_cnt=%u&tnp_check_login_fail_cnt=%u&tnp_connect_success_cnt=%u&tnp_immediate_bitrate=%u
http://log.xiaoyi.com/info.gif?p=home_v1&sysVersion=%s&mac=%s&key=%d&didm=%d&sn=%d&tfstat=%d&hdSize=%d&hdLeftSize=%d&silentmode=%d&lightmode=%d&isdaymode=%d&packetloss=%d&out_packetloss=%d&is_video_viewing=%d&p2pconnect=%d&p2pconnect_success=%d&ssid=%s&bssid=%s&ptz_horizontal_flip=%d&workmod=%d&doreset=%d&xiaomirouter=%d&bind_success=%d&start_with_reset=%d&miio_send=%d&miio_recv=%d&motion=%d&p2ptype=%d&alarm_enable=%d&record_num=%d&systick=%u&video=%d&pic=%d&gen_url_fail=%d&gen_url=%d&ban_dev=%d&cgi_check_mirouter_ok_cnt=%u&nslookup_check_mirouter_ok_cnt=%u&tnp_init_status=%d&tnp_p2p_mode_cnt=%u&tnp_relay_mode_cnt=%u&tnp_check_login_success_cnt=%u&tnp_check_login_fail_cnt=%u&tnp_connect_success_cnt=%u&tnp_immediate_bitrate=%u
%s -c 311 -url https://api.xiaoyi.com/v4/ipc/check_did -uid %s -keySec %s
%s -c 139 -keySec %s -url https://api.xiaoyi.com/v4/ipc/reset -uid %s -version %s -mac %s
/home/cloudAPI -c 301 -url “https://api.xiaoyi.com/vmanager/upgrade/get_md5”
%s -c 140 -url https://api.xiaoyi.com/vmanager/upgrade -uid %s -version %s
/home/curl http://%s/cgi-bin/luci/api/xqsystem/init_info | grep routerId | wc -l
%s -c 141 -url https://api.xiaoyi.com/v4/tnp/on_line -keySec %s -uid %s -version %s
%s -c 304 -url https://api.xiaoyi.com/v4/alert/event -uid %s -keySec %s -EventTime %lu -EventStat %s -pic_url “%s” -video_url “%s” -pic_pwd “%s” -video_pwd “%s”
%s -c 138 -key %s -keySec %s -url https://api.xiaoyi.com/v4/ipc/on_line -uid %s -version %s -mac %s -packetloss %d -p2pconnect %d -p2pconnect_success %d -tfstat %d
%s -c 136 -url http://api.xiaoyi.com/v2/ipc/sync_time
%s -c 310 -url https://device.io.mi.com/ot/register -uid %s -vendor %s -timestamp %lu -token %s
It is using another approach to avoid the device check as the “https://api.xiaoyi.com/v4/ipc/check_did” is still in the file.
Hi everyone,
I have made my camera (CNxx160622 hardware with FW 1.8.6.1C or 1.8.6.1Q) working outside China.
And I want to share my finds.
1. Serial port for CNxx160622
Check the following image. There are 3 contact points, and I connect to board via the 3 contact points, not from the 4 pin connector.
TTL voltage level is 3.3v, and baud rate is 115200.
https://postimg.org/image/4otv61lyl/
2. For 1.8.6.1C, there is a factory test script. And if you put a script on SD card and path is “test/factory_test.sh”, then the script be execute automatically after the camera booted. But the script is removed on 1.8.6.1Q.
3. I wrote a scrip to make the camera work again outside China.
Download the file, and decompress it to root of SD card.
https://mega.nz/#!bEwzXJ7J!iyiUTEW8ojOrOqBh4zLNKQpktlaqbPwuDZdL-7jBcus
If your device’s FW is 1.8.6.1C, you just need to insert the SD card into your camera, and it will hack your device automatically, when it finished, the camera will reboot automatically, then your camera is free.
If your device’s FW is 1.8.6.1Q, you need to connect your camera via serial port to get console, then insert the SD card into your camera, when you see the command prompt, just type “/tmp/sd/hack_yi.sh”, then your camera is free.
I forgot to write the pin definition for serial port.
On the image, the pins from left to right it TX, RX, GND.
Is it should be from Right to Left: TX, RX and GND?
If your camera still not work after applying the patch, please reset it and connect it via Mi Home again.
hi, great to heard that your finding make it worked. Can you share if you have the connection and cable in picture?
Thanks..
Dear JonesChi,
thanks for sharing 🙂
very helpful
maybe u have solve the 22CN too :p
if yes please share if u dont mind
thanks a lot 🙂
Im newbie here, what tools to connect 3 contact points on the board?
Thank you very much! It is very helpful!
It work! My fw is 1.8.6.1C. It only take second to hack with your script. Thank you very much. For others can try this script, very easy to do
how i can know which firmware in my camera for 17CNxx160622 used ( after pair app camera is turn off and can’t see firmware in app
had try to used you hack firmware but camera not reboot waiting 10 min still orange light
then turn off and turn on and try pair with app (yi home and mi home) this time can pair no say can’t used outside china but in app error -3006 who is same problem with me
Hi, do i need a speciL serial port connector?
where can buy the serial port connector?
Appreciate you can guide step by step to show us.
Thank you..
Aggreedd
I am newbie here
Can u guide me step by step how to do it
Especially the connection to 3 port
🙂
Hi Jones,
I updated my cam to a 1.8.6.1C version and I’m putting the script into a SD card root folder. It seems like it doesn’t do anything just yet, camera still says “This camera can only be used within China”.
I tried it on 2 devices
12CN danger dangerxx160122
12CN danger danger160408
12CN can use the equip_test.sh script. Not the factory_test.sh
Hi JonesChi,
Thanks for the code you provided on https://mega.nz/#!bEwzXJ7J!iyiUTEW8ojOrOqBh4zLNKQpktlaqbPwuDZdL-7jBcus
It worked well on me for 17CN dangerx version.
But I tried on 22CN dangerx version can’t worked, do you have any idea or another code for it ?
dont have robin… what production is that? newest one? i buy on august anyway.. and not all my goods come into my hand now.. so i need to wait… bdw u buy 22CN when,…
any one can help?
Hi, is there any chance you could show step by step how to connect serial port connector to the camera?
Maybe you could share a video tutorial or something so noobs like me can get a better picture on how to do it properly?
Amazing.
This script worked for me!
i got the serial port device. how to get the command prompt? i have connected to the 3 pin. but nothing prompt on my mac/pc
anyone pls help
Your script works however how do you enable telnet on 1.8.6.1C firmware?
Hi Jonas, you know how to change chinese speaking to english speaking for Xiaoyi camera CN17 version.
Anyone solved the 17cn issue?
Please share here
Need help 😐😑
Hi, Debby!
Yes, this problem is solved by JonesChi.
…
I wrote a scrip to make the camera work again outside China.
Download the file, and decompress it to root of SD card.
https://mega.nz/#!bEwzXJ7J!iyiUTEW8ojOrOqBh4zLNKQpktlaqbPwuDZdL-7jBcus
If your device’s FW is 1.8.6.1C, you just need to insert the SD card into your camera, and it will hack your device automatically, when it finished, the camera will reboot automatically, then your camera is free.
If your device’s FW is 1.8.6.1Q, you need to connect your camera via serial port to get console, then insert the SD card into your camera, when you see the command prompt, just type “/tmp/sd/hack_yi.sh”, then your camera is free.
Wooooowww thanks a lot
Will try it
Thanks a lot if any problem can i contact you here?
Thanks for helping
Dear romachand, are u indonesian? 🙂
Debby,
Are u Indonesian ?
17CN can follow jonashchi, u have 22CN btw ?
dear romachan,
can u help me?
because i have do the step above and still voice out this camera can only be used within china…
and i cant check my firmware because loading all the time.
can u help me?
very appreciate if u want to share your contact no in my email [email protected]
thanks a lot
thanks work FOR ME 17CNYUGXXIWP16 danger11 i use the sd card
Hi Jonesville
How much time will it take to reboot???
Extremely Sorry JonesChi for misspell name(Android auto correct error)
Hi JonesChi
It worked Wow… With your script
Without serial port
Thanks a lot
:)☺
By the way the camera rebooted in 30sec I thought it would take some time so I waited for 10min during the time the light was stable orange (as it was in the beginning of starting the camera with 8gb memory card having your above mentioned script )
Thanks again
Next time I promise I will check reviews of Chinese products before buying :)😊
i try this patch but not work, only yello light on no reboot.
after this i can not flash new firmware, sd-card flash still blockt ???
my camera after hack not reboot after 5-10 min still stable orange then turn off and turn on
but had try to pair with app can pair no sound can’t used out side china but error -3006
please give me and idea
used yi home mi home
hack with jones chi file
I have same problem with you john
do you have way to solve -3006 ??? if you have way ple share to me tks.
All those guys who are in trouble please remember to remove memory card after the script finished
Any suggestions for apps in English language which supports this camera, and switching off blue light
And camera mounting ideas
Using yi home app I can do a lot and it’s in English too
Hello,
1 – every reboot giving error ” waiting for connection ” how to fix him ?
2 – How do I turn off the sound ?
Hi I’ve this camera, China version.So far it was working well, but after my android phone was upgraded to version 6.0.1, it couldn’t pair anymore.
Is it any patch to support this camera on new android version?
Any advice pls
Thanks
Herman
Many thanks to JonesChi
Now my camera working like charm , thanks for sharing the script
Any chance to downgrade the camera so they can speak english again?
thanks
Thanks JonesChi and thank Larry!!!!
The script is ok and run my new camera.. Thanks !!!!!!!!!!
i have FW 1.8.6.1C and tried the patch from JonesChi, copy all files to sd-card, but only yello light on and no reboot.
after this i can not flash again from sd-card new firmware ?????
Thanks JonesChi!
Is there any way to enable telnet, rstp, change timezone on CNxx160622 device unlocked by your script?
Hi have a couple of noob questions
– Where is the model number listed i.e. (12CN danger dangerxx160122, 12CN danger danger160408)?
The only number I can find on my camera is 17CNYFS998, which doesn’t fit with what people are posting here.
– How do I determine the current firmware version running on my camera?
It seems finding out this information is a prerequisite as the process is different depending on when the the type and firmware version.
Thanks
the long model number you can get by scanning the qr code behind the camera. but for the firmware, im trying to figure out too. how to know it since i cant access the locked camera (17CN).
used qr code app to scan at barcode at back side of camera
Thanks, that was very helpful.
@Z-ster
this is code u can find on the back of camera.
if yours is 17cn u can use the script from JonesChi
it will help u to connect.
But u need to check wether it comes with firmware C or Q
thanks
and how to check the firmware?
Thanks, I’ve worked out my number is 17CN danger dangerX160622, but I’m still unable to determine what firmware the camera is running.
Thanks,
John
So once the flash is successful in unlocking the camera with the method given above by JonesChi, will I need to install new firmware as the next step? If so which International version firmware should I be installing? I live in Australia.
Thanks
John.
HI
I used JonesChi FW… it take 20 min to restart.
after that i connect it shows (camara not online -3006)
HELP
and how to check FW?
Thanks in advance
@ La Be
you can while camera already connected, eventhough they said only can be used within china, you check on the setting, it will show what firmware they used
thanks
i cant, right after i pair the camera, the camera continously say this camera can only be used within china and when i open the app, it says the camera is offline (-3006) and when i go to settings it says failed to connect, cannot get more information.
HI
I used the hack and now when i connect to MI HOME it show this
http://postimg.org/image/hvm41c8dx/
and my ver. is this
http://postimg.org/image/bnhtrv70l/
any one of you know what’s the problem?
thanks in advance!
Same for me La Be..
I think i need to do 3 points serial port method to make it work
Bought in xiaomi store in china
Anyone got this problem with mi home(v3.1.2) in ios version 9.3.2?
It’s doesn’t show the orange strip in timeline, then it’s can not watch backward.
While it can work well in android.
hi yi master, kindly share serial port method step by step. really appreciate.
@jax
you still have firmware C, so u can use the files without using port cable. extract the files from Jones Chi and should be able to use the camera
How to see the firmware status?
I have go to setting but no information there
Can not connect to camera at all.
Please help
My version is B is there any way i can upgrade to C and use Jones Chi method? because i couldnt find fireware C anywhere on internet. However i can find Q but i dont know how to do that port cable method. Can someone please post a step by step guide for that method?
i have usb to tel cable ready.
anyone can explain further? how to get console? anyone have image to refer?
Has anyone solved the problems with rewinding the video of YI Home?
With the last Q firmware and cameras made after 2016 june 29, it is impossible to execute any step of this tutorial. Perhaps the only possible solution is through a serial phisical link. But I cannot find a clear and simple tutorial about it.
I’ve tried out the script by JonesChi. Well, for the first time the cam has had a different behaviour: all other scripts were completely ignored, but this one was read because the yellow light stopped blinking and remains lit for over 20 minutes. After that time the cam has rebooted but nothing changed. It remain banned. So I opened the microsd into the reader and looked into the file log_init.tar.gz – tmp – init – homever. There I’ve sadly read “1.8.6.1Q_201607271501”. So I discovered that my fw is a Q version. Now I have to find a clear tuorial for the serial link procedure but the good news is that for the first time a script into the microsd was not ignored. Perhaps there is a possibility to solve this puzzle through a software hack. Perhaps.
Congrats to JonasChi my cam now is online. I have a 17CN with Q firmware. So your script works with this fw too