Have you ever wanted to become a hacker or to experience the thrill when you gain root access on a government vulnerable server?
I always thought security was the exclusive society of some cyber elite who were finding exploits before they could walk. But the truth is, if you have the passion and determination to learn, you can become a professional ethical hacker.
So, I decided to learn more about cyber security. However, I had no idea where to start but I knew that I really loved solving puzzles. At a local security meetup, I came across some CTF challenges, security puzzles, and I had a mission to solve them all.
One way to do cyber security training is by attending a cyber security Capture the Flag (CTF) event. These present a series challenges which will help you understand how hackers are able to compromise the security defences of different systems/applications, and how to defend against them. CTFs are used as a learning tool for anyone that is interested in cyber security.
Whether you are new to computer security or are a veteran, Capture the Flag competitions are a great way to both learn new skills and hone existing ones.
CTF competitions are a series of computer security challenges, with individuals or teams competing to solve the most challenges and earn the most points.
These challenges are often based on real-world incidents/vulnerabilities that give you a chance to experience how it’s actually done and better prepare you to defend your own systems from these types of attacks. So not only are CTF events fun, but they can also be educational and professionally rewarding.
There are usually two types of CTF events, attack-defence (red team/blue team) and Jeopardy-style (Red Team).
The attack-defend CTF is where the red team attacks the other team’s system to capture flags while the blue team defends their own system.
The Jeopardy-style CTF usually involves one or more people, working alone or on a team, who attempt to capture various flags while there is no team defending them. Some of the challenges can be done against a main server that was developed for the CTF and the flag is inputted into the CTF scoreboard to get points for the team.
There are multiple formats and styles of CTF, but they all have one thing in common – the challenges. Players are presented with puzzles, programs with security vulnerabilities, or systems to break into. Embedded in the puzzle, program, or system, is a secret key, or “flag”. Finding this flag is proof that you solved the puzzle, and submitting it to the scoreboard earns your team points. Flags are typically chosen to look very distinctive, so that when you see one, you’ll know it’s a flag, and that you’ve solved the puzzle. Flags will tend to be a phrase or sentence in the form of flag{mysecretfl@g}.
There’s a wide variety of challenges that show up in a CTF, but they tend to be grouped into a few categories:
Web – Exploiting web pages to find the flag
These challenges involve attacking common vulnerabilities in web technology. For example, you might need to use SQL injection to read the “secret_flag” table of a database, use directory traversal to get a web server to serve you “flag.txt”, use Cross-Site Scripting to trick a simulated user to send you their password, or bypass some client-side checks implemented by obfuscated javascript
Cryptography – Typically involves decrypting or encrypting a piece of data
Steganography – Tasked with finding information hidden in files or images
Binary – Reverse engineering or exploiting a binary file
Binary: Pwnables – Exploiting a server to find the flag
Binary: Crackmes
Digital Forensics
Packet Analysis – typically analyse a packet capture dump
Miscellaneous
Well, the wait is over! I have put together the infrastructure, a playground, where you can put your hacking skills at test or start from scratch. Ask you company to reach out to me and I can work with them to set up the challenges for you.
Should you be an expert or a beginner you will find a challenge to learn new skills from. I think all developers can benefit from learning some basic hacking if only for the sole reason to better understand how to write secure code.
Excited? Read on.
There are 54 challenges waiting to be cracked. Each challenge will reveal a flag{} that once submitted will reward you with points. The individual or team with the most point will win a cool price.
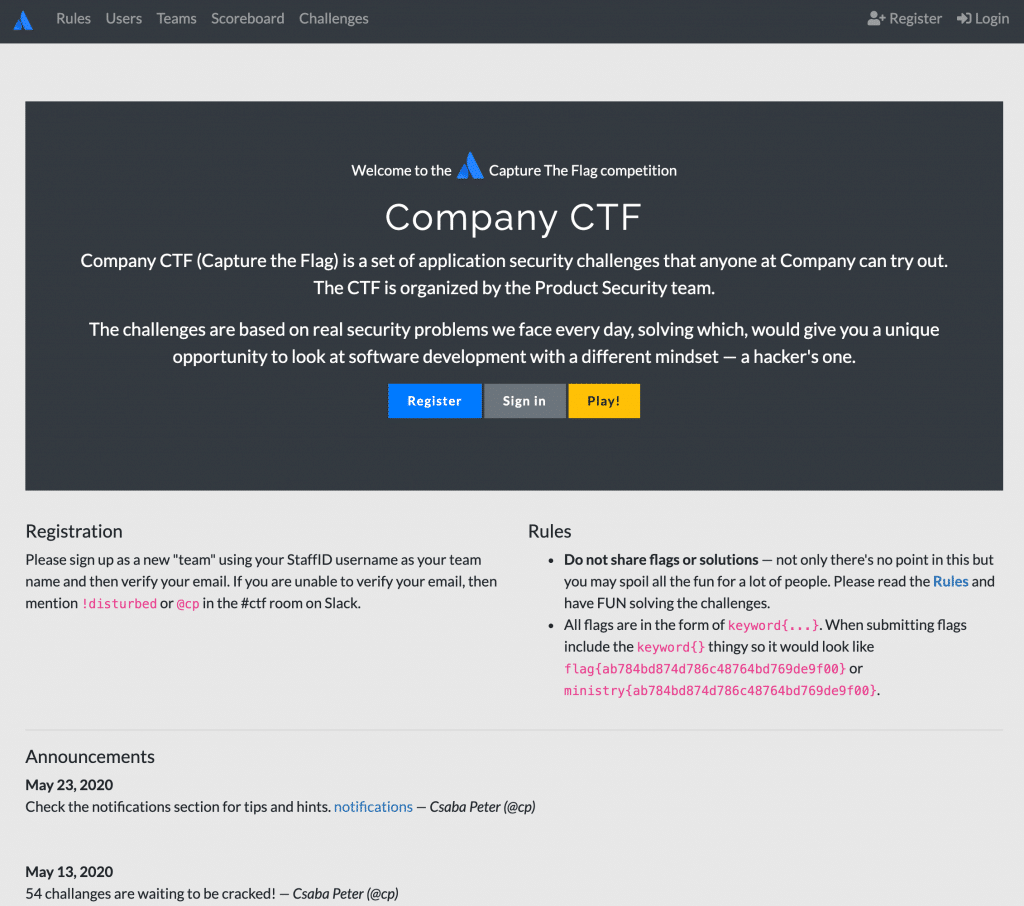
Registration
While you can participate solo, you’ll probably have a much better time if you play with a team. Get a few friends, sit down, and work together to solve challenges. After the beginning of the game, there’s multiple challenges open, so each person can work on their own, or they can try to collaborate to solve one.
Virtual Machines are suggested for doing CTF challenges because they allow you to preserve and protect your host machine. As best practice do not reuse your password.
These challenges were written by people, and these people want to see the challenges solved. If you get stuck, it can be worth asking for a hint, especially if you have a good idea of what you’ve tried so far and what you’re stuck on. Sometimes, just talking aloud with the author is a good way of getting that burst of inspiration. The author can also point out if you’re on the right track, or way off base.
If you get stuck, you can always take a break, try a different challenge, and come back to this challenge later.
Make copious use of Google.
If you’re programming, minimizing the time spent coding is your goal. You’re writing code that will be used once. Maintainability, readability, and robustness aren’t concerns. Make it pretty for the writeup later. Python has a nice set of libraries you can use for CTF challenges, like pwntools.
Linux shell utilities are your friend. I’ve solved many challenges with one-liners. Read up about imagemagick, pbmtools, sox, sed, awk, grep, strings, file, xxd, sort and uniq.
Some other teams may prank or troll you. This can be all in good fun, but it helps to have a thick skin about these kinds of things. Prank or troll them back! But please also be reasonable, and don’t do anything that causes lasting damage. If you feel another team has really crossed the line, talk to the contest organizers.
Have Fun!
defendtheweb.net – is an accessible gamified hacking intro.
application.security – interactive tutorial OWASP Top 10
avatao.com – online security training platform that offers hands-on exercises
Microcorruption.com – a terrific way to learn about assembly hacking and buffer overflows.
Vulnhub.com – will expose you to tools of the trade like nmap
https://portswigger.net/web-security – Free, online web security training from the creators of Burp Suite
Pentesterlabs.com – offers a lot of short lessons on specific attack paths. You can use your self directed learning budget if you want to access the pro exercises.
Hackthebox.eu – has a ton of high quality, free, vulnerable machines.
Offensive Security – offers in depth courses and certification, speak to your manager about using some of your manager approved education allowance to attempt some of their certifications (find out more in #offsec on slack).
binwalk – Analyze and extract files (my favourite)
burp suite – Feature packed web penetration testing framework
stegsolve – Pass various filters over images to look for hidden text
GDB – Binary debugger
apktool, jadx – reverse engineering Android apps
CyberChef – a web app for encryption, encoding, compression and data analysis
The command line 🙂
Virtual Machines
Virtual Machines are suggested for doing CTF challenges because they allow you to preserve and protect your host machine. You’ll need to provide your own licenses for the operating systems, where required.
Kali Linux
Kali is a specialized version of Linux (or distribution in the Linux vocabulary) that is focused on penetration testing. It’s free to download and there are paid training exercises available from the official site.
https://www.kali.org/
Microsoft (offers some developer virtual machines with limited licenses):
https://developer.microsoft.com/en-us/windows/downloads/virtual-machines
VirtualBox:
https://www.virtualbox.org/
VMWare:
https://www.vmware.com/ca.html
Hex Editor
HxD (Windows GUI):
https://mh-nexus.de/en/hxd/
xxd (Linux command line):
https://www.oreilly.com/library/view/linux-pocket-guide/9780596806347/re28.html
Hex Fiend (MacOS):
https://www.macupdate.com/app/mac/22589/hex-fiend
0xED
You can install it with brew: brew cask install 0xed
Mobile Phone Analysis
Apktool – https://ibotpeaches.github.io/Apktool/
A tool for reverse engineering 3rd party, closed, binary Android apps.
Jadx
jadx – Dex to Java decompiler
Passionfruit – https://github.com/chaitin/passionfruit
It’s an instrumentation toolkit for developers, reverse-engineers, and security researchers.
Plist* (property list) file reader
Plists are a common file type on Apple devices
iCopyBot (Windows):
http://www.icopybot.com/plist-editor.htm
Plist editor Pro (Windows):
https://softfamous.com/plist-editor-pro/
Plist Edit Pro (MacOS):
https://www.fatcatsoftware.com/plisteditpro/
Network Traffic Analysis (Packet Analysis)
WireShark:
https://www.wireshark.org/
Hex Packet Decoder / Network packet decoder
https://hpd.gasmi.net/
CyberChef – The Cyber Swiss Army Knife – a web app for encryption, encoding, compression and data analysis
https://gchq.github.io/CyberChef
CloudShark (cloud-based equivalent to WireShark):
https://www.cloudshark.org
TCPDump (Linux):
https://download.cnet.com/Tcpdump-for-Linux/3000-2383_4-75185857.html
BurpSuite (Linux) (Community Edition)
https://portswigger.net/burp
Password Cracking
John the Ripper:
https://www.openwall.com/john/
HashCat:
https://hashcat.net/hashcat/
Rainbow Tables*:
http://project-rainbowcrack.com/table.htm
Files containing lists of words and/or passwords. They can be used in conjunction with other tools for brute force attacks.
Malware Analysis Environment
SANS Sift workstation (VM):
https://digital-forensics.sans.org/community/downloads
Includes hundreds of tools, including malware analysis utilities
SANS white-paper on Malware Analysis:
https://www.sans.org/reading-room/whitepapers/malicious/malware-analysis-introduction-2103
See page 25–28 for a list of tools
VirusTotal:
https://www.virustotal.com/#/home/upload
Upload a file and see how likely it is to be malicious
Memory Analysis
Volatility:
https://www.volatilityfoundation.org/
iTunes backup reader
iFunBox:
http://www.i-funbox.com/
Android backup
Android Backup Extractor:
https://sourceforge.net/projects/adbextractor/
Forensic Image Reader(s)
FTK Imager (GUI):
https://accessdata.com/product-download
Autopsy(GUI)/TSK (The Sleuth Kit) (Command Line): https://www.sleuthkit.org/autopsy/
SANS Sift workstation (VM):
https://digital-forensics.sans.org/community/downloads
Includes hundreds of tools, including image parsing utilities